The author is a marketing and technical communications specialist for Tieline.
It has never been more important to ensure broadcasters employ vigilant IT cybersecurity protocols in broadcast plants. If you are connected to the internet, you are at risk.
As unbelievable as it seems, many broadcasters still have a laissez-faire attitude to IP network security. Why?
Some of the main reasons for this include:
- An incomplete strategic threat analysis.
- Underinvestment in adequate security systems across the network.
- A lack of investment in adequate human resources and training.
In the past, the broadcast plant was somewhat protected from external intrusions. Wayne Pecena from Texas A&M University is a frequent lecturer on IP networking and cybersecurity to the broadcast industry. “The broadcast technical plant has been relatively immune from cybersecurity threats as the traditional baseband signal design was difficult to penetrate from outside the station,” said Pecena. “Overpowering a traditional STL path required very specific equipment located at a very specific location.”
Given the integrated nature of broadcast and the IP world today, this is no longer the case.
WHY CYBERSECURITY IS IMPORTANT
All broadcast operations these days are vulnerable to cyberattacks and some of the more obvious reasons to implement and maintain network cybersecurity include:
- Protecting a company’s assets: Threats include hackers, computer viruses, Trojan horses, worms, spyware, Denial of Service (DoS) attacks and more.
- Staying on-air: If hardware is disabled by security threats it can take your network off-the-air!
- Complying with broadcast regulations: Hackers have previously been able to take control of certain unsecured devices and maliciously streamed content.
“Cybersecurity threats and mitigation’s must be addressed in a proactive manner by the broadcast engineer to allow the broadcast station to take advantage of the cost savings, features, and services offered by an IP based IT infrastructure,” said Pecena.
These days it pays to be especially vigilant. Government agencies and the banking sector have often led the way with cybersecurity and broadcasters must apply the same level of vigilance.
THE LAYERED APPROACH
As studios have transitioned to IP-based environments a strategic approach to cybersecurity is essential. Broadcasting products are increasingly computer-based running Linux or Windows and controlled using browsers over a variety of IP networks. Utilizing a firewall on its own is simply not enough.
A “Layered Approach” to cybersecurity establishes security on several levels. Wayne Pecena recommends using the Data Flow aspects of the OSI model as an implementation guide:
- Layer 1: Physical Access — Restrict physical access to network infrastructure and control and monitor electronic access.
- Layer 2: Data Link — Control hosts that can connect to your equipment, e.g. port and MAC Address restrictions. Disable unused ports.
- Layer 3: Network — Network equipment security features such as Access Control Lists (ACL) e.g. administrator and lower level access, Firewalls, secure connectivity (IPSec) and application security.
- Layer 4: Transport — Implement TLS/SSL security.
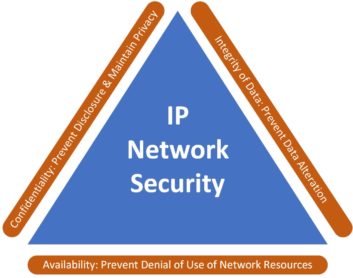
This approach helps to ensure the Confidentiality, Integrity and Availability (CIA) triad of Network Security Goals is achieved.
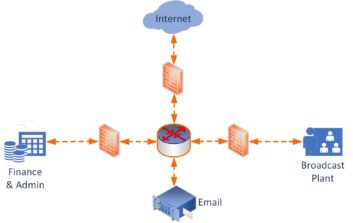
SECURITY ZONES
A segmented network architecture adds another layer of security to your network. Zones with independent security layers make it much less likely that breaches will occur. It also helps quarantine areas if there is a security breach in one zone. To achieve this, consider separating broadcast content and transmissions from financial, admin and email functions within a broadcast facility.
GLOBAL PERSPECTIVE
Charlie Gawley, Tieline’s VP Sales APAC/EMEA, has visited more broadcast plants than most. He has worked closely with broadcasters in Europe, Asia and Australia, advising on streaming live audio over the internet with a variety of IP technologies.
“I have noticed that in the past 10 years many engineers’ attitudes to cybersecurity have moved from somewhere between ‘blasé and somewhat interested’ to being ‘highly concerned’ about network intrusions from nefarious characters,” said Gawley. “There is no doubt this correlates with the growth in reliance on IP throughout the broadcast plant.”
“As a manufacturer of devices that are very often connected to the open internet, Tieline believes in continual development of security features to avoid ever-present and continually evolving threats,” he said. “These days broadcasters are not only asking more questions about the security features in our products, they also offer suggestions and actively engage in developing network cybersecurity strategies before their product is shipped. Forewarned is forearmed as they say.”

BEST PRACTICE
Tim Neese from MultiTech Consulting, Inc., is a broadcast systems integrator with clients throughout the U.S. When connecting Tieline codecs to the internet he recommends a range of security procedures.
“We always recommend clients take full advantage of the built-in security options, have a schedule for password changes, and make use of a firewall. The ability to implement SSL connections is a great addition to the built-in feature set and in many cases removes the need for a VPN connection to securely administrate the codec. For point-to-point connections, we recommend limiting, via a firewall, the IP addresses that can connect to the codecs. In all situations, open only the necessary ports, maintain and review logs of connections and connection attempts, and implement firewall monitoring that generates alarms for excessive traffic on administrative addresses/ports.”
[Read: IBC Exhibitor Viewpoint: Charlie Gawley, Tieline]
Finally, it may seem obvious, but ensure you use secure and high-quality passwords to reduce the chance of passwords being compromised across your network. Using a good quality password manager helps to create strong and unique passwords. In addition, when an employee leaves your organization be sure to kill off all their passwords and create new ones for any shared accounts.
WHERE TO FROM HERE?
This is well summed up by Wayne Pecena. “We are all aware of the advantages offered as the traditional baseband broadcast plant is transitioned to an Information Technology (IT) infrastructure based upon Internet Protocol (IP) transport. What is often not mentioned or even ignored is the downside. As an IT system, cybersecurity can no longer be an afterthought and must be a top of mind concern for the broadcast engineer. The broadcast plant is no longer immune to cybersecurity threats. Cybersecurity concerns will only continue as the traditional rack room environment becomes an IT system, which may well live in the ‘cloud’ whether on premise or not.”
If you want to ramp up your IP cybersecurity knowledge base the NAB has a good program, which offers an introduction to cybersecurity and the challenges faced in the broadcast station environment.
For more information see https://www.pathlms.com/courses?category_ids%5B%5D=2109&slug=nab